Solution
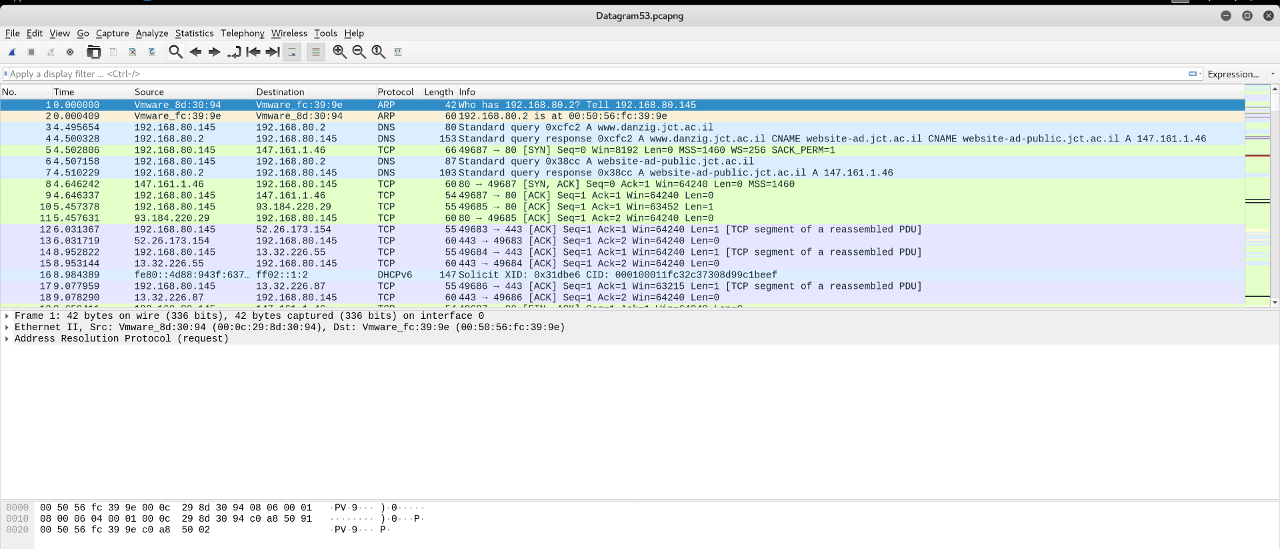
Firstly, we opened the Datagram53.pcapng with wireshark and started to look for something unusual.
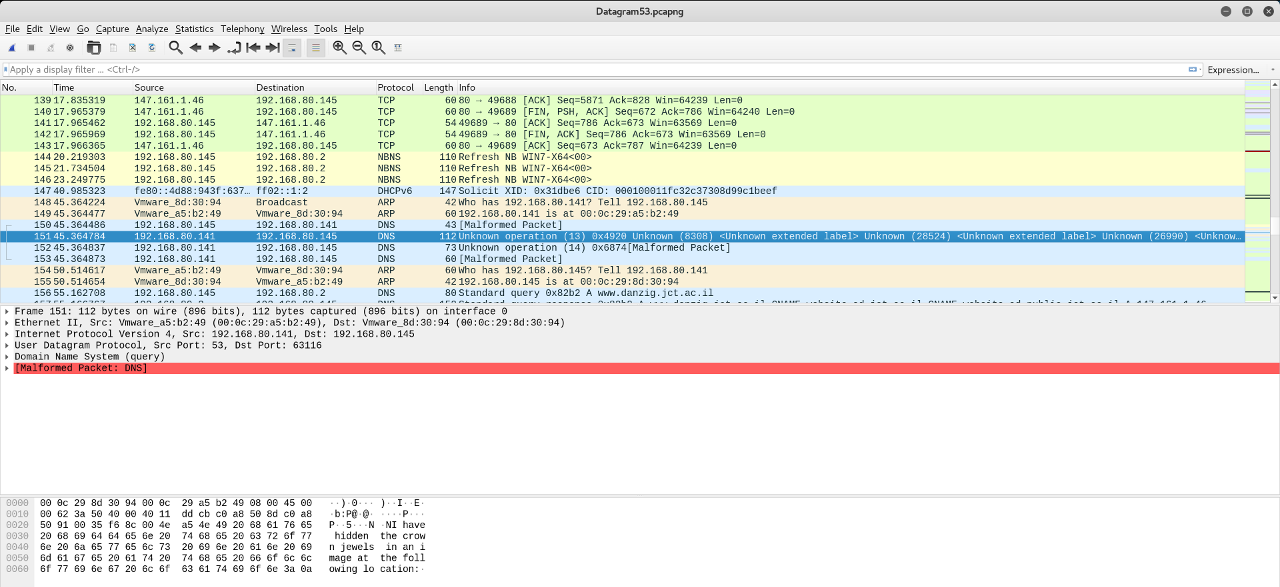
As we proceeded we saw some Unknown DNS packages.
After I looked into them I saw these messages:
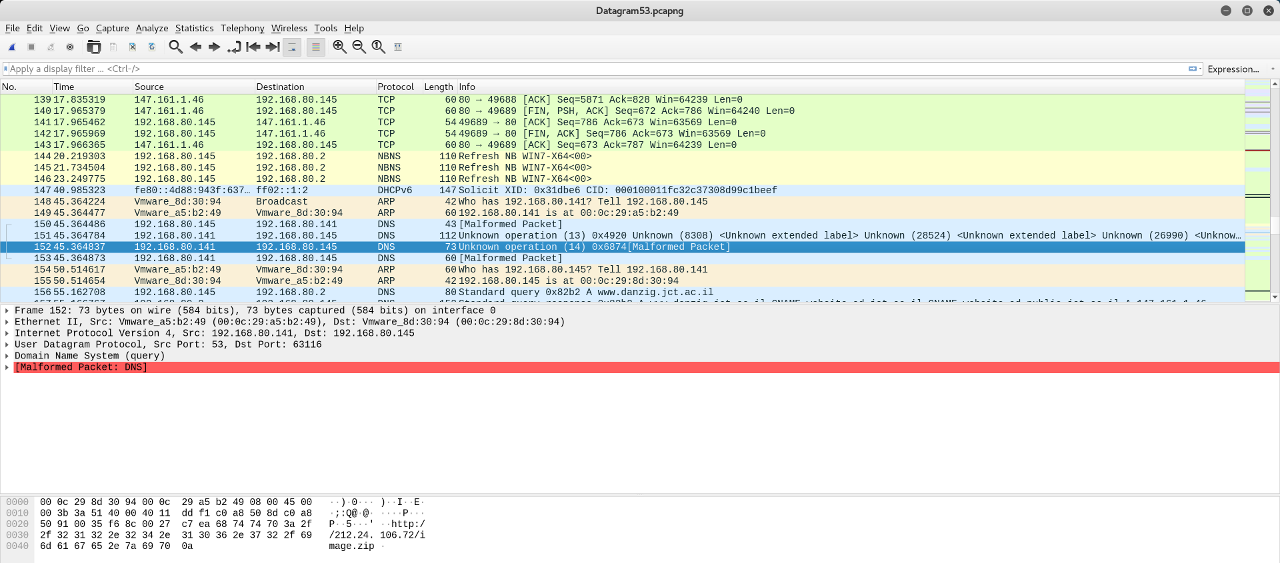
"I have hidden the crown jewels in an image at the"following location:
http://212.24.106.72/image.zip"
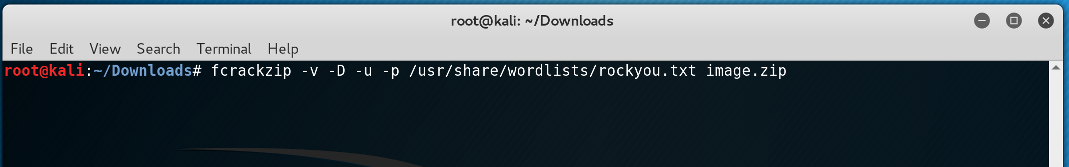
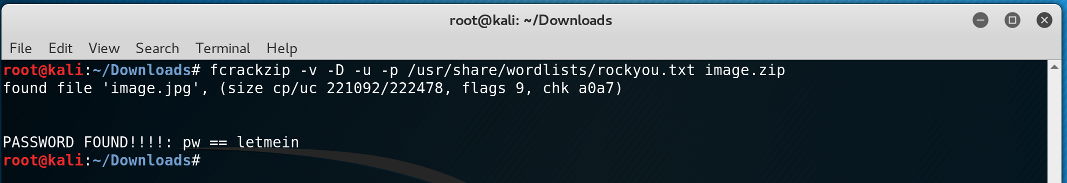
The zip that we downloaded was locked, so I used frcrackzip and rockyou wordlist to crack the password.
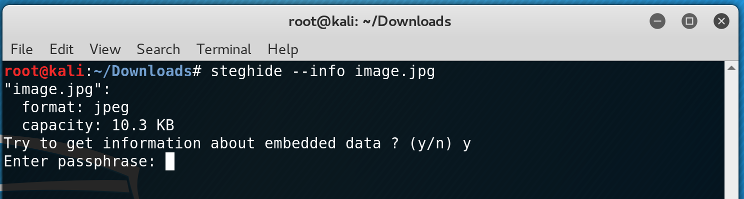
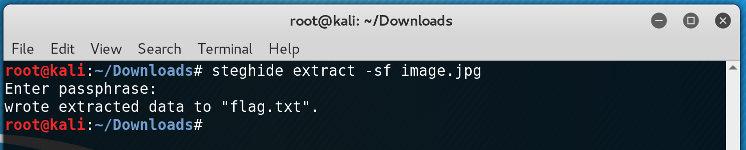
I checked the image for any hidden file...
..and again, I had to find another password.
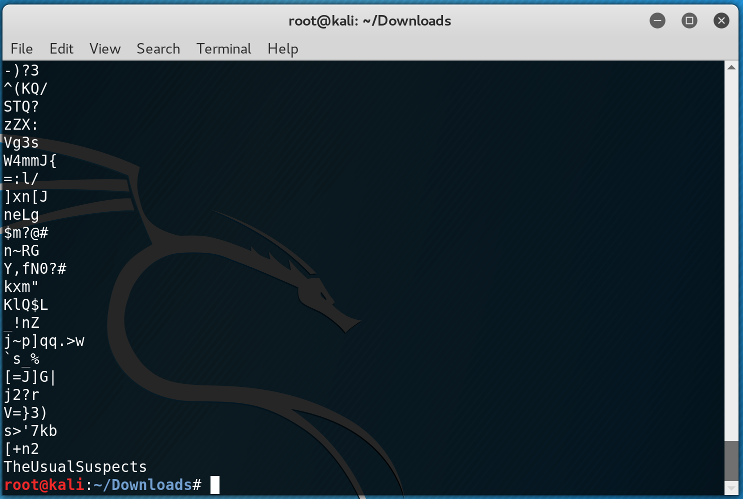
So I checked the image for any possible hints or a password, in case they were hidden inside the image, by printing the strings of printable characters.
At first I was confused, so I tried to change the brightness of the image and see if there were any hidden messages, but still nothing. Hmm... I stop for a moment and try to relax. A few moments later I decided to try the last line of the strings as a password.
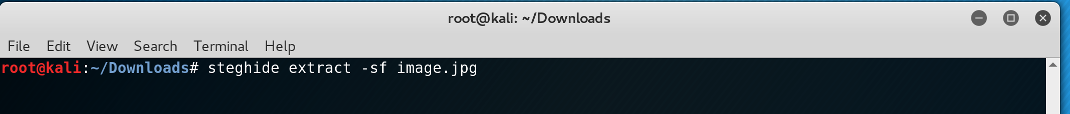
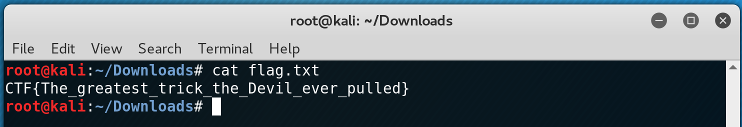
And that was it. We had successfully extracted the file that was inside the image! I printed the content of the flag.txt and...!