Solution
The ext4 is a journaling file system for Linux. The only thing we had to do was to mount the ext4 partition into a Linux VM.
Hmm... We needed a passphrase... At first I started to look how can I crack this passphrase. But after a while I read again the description and realized that all we needed was there.
I jumped back to the Autopsy and started to go through every directory and opened every file, maybe we have missed something.
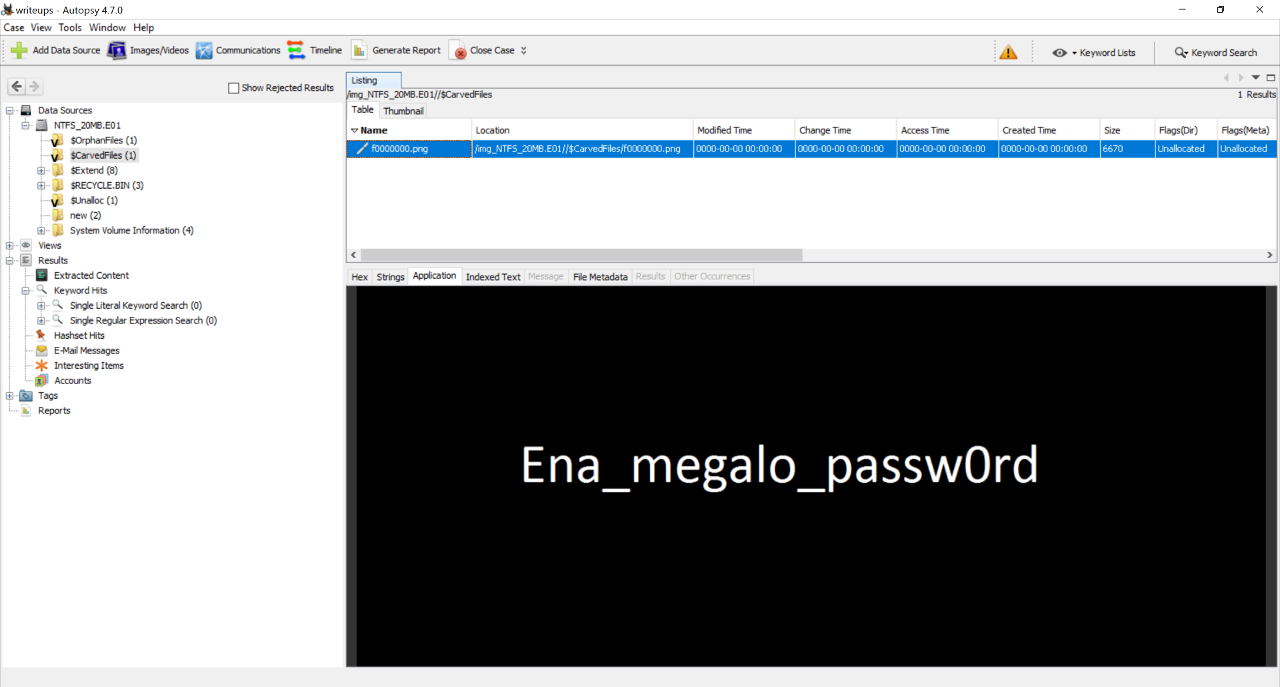
"Ena_megalo_passw0rd" So One_big_password 😜. I tryed with this and...
We have successfully mounted the ext4 partition. I looked inside and the flag was found.