Solution
First we started by setting up the Autopsy to be ready to load the NTFS image.
Then we loaded the NTFS image.
At this point everything was set up to start our investigation. From the description we know that the first flag for this challenge is found where files go to be deleted in the NTFS image.
So I started to navigate into the Recycle bin.
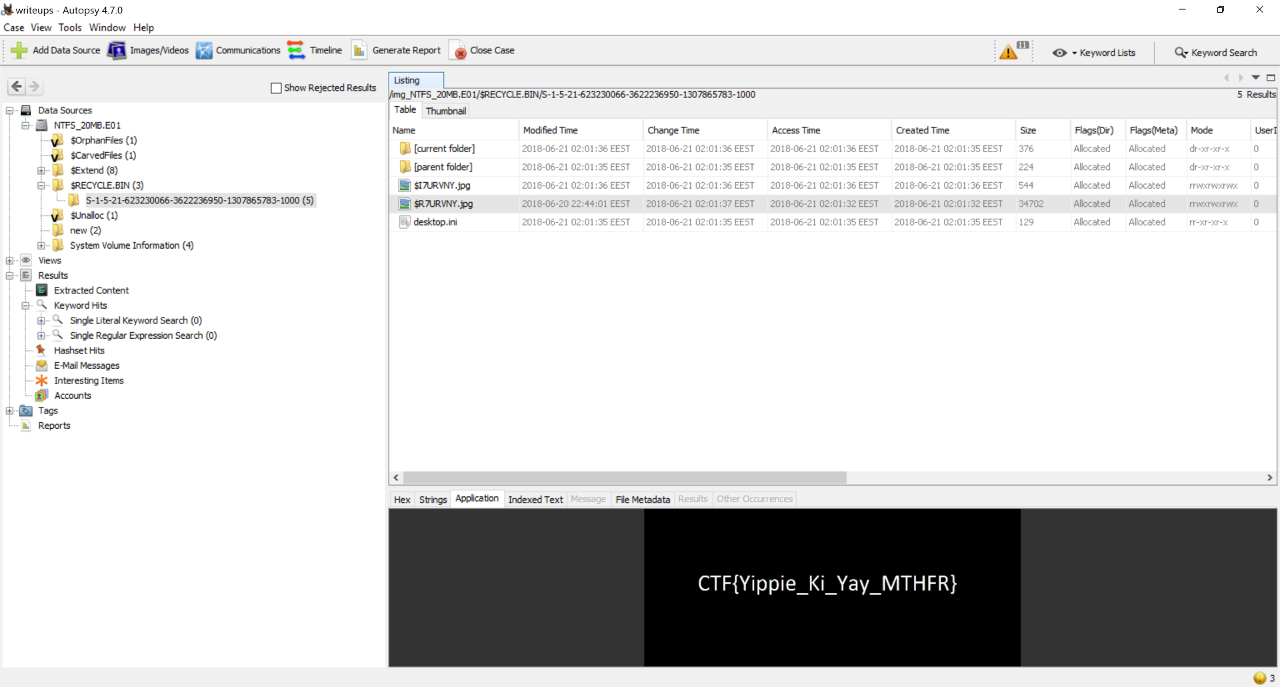
And, as expected, the flag was in Recycle bin at jpg image.
CTF{Yippie_Ki_Yay_MTHFR}